Why you should care about HTTPS and how to get it for free
14 Jun 2016Web browser makers are encouraging the use of HTTPS over traditional HTTP. Chrome only supports geolocatiozation and web RTC over HTTPS. Firefox, Chrome, MS Edge only supports HTTP 2.0 for secured sites.
Plain old HTTP is no longer good enough for them anymore. Why? To understand their motivations, we should take a look at the unsecured nature of the internet.
The network by itself is not secured
If I want to google something, behind the scene this is what happened:
[/home/thach] traceroute google.com
traceroute to google.com (216.58.198.174), 30 hops max, 60 byte packets
1 livebox.home (192.168.1.1) 2.140 ms 3.921 ms 3.847 ms
2 80.10.232.225 (80.10.232.225) 7.877 ms 8.927 ms 8.905 ms
3 ae101-0.ncgre202.Grenoble.francetelecom.net (193.253.85.42) 8.856 ms 8.807 ms 8.738 ms
4 ae49-0.nilyo102.Lyon.francetelecom.net (193.252.101.134) 9.923 ms 9.884 ms 9.836 ms
5 81.253.184.82 (81.253.184.82) 24.124 ms 25.413 ms 25.357 ms
6 81.52.186.142 (81.52.186.142) 15.111 ms 10.417 ms 9.893 ms
7 209.85.252.36 (209.85.252.36) 10.726 ms 209.85.252.194 (209.85.252.194) 11.089 ms 209.85.252.36 (209.85.252.36) 11.345 ms
8 216.239.58.1 (216.239.58.1) 18.451 ms 209.85.143.219 (209.85.143.219) 28.290 ms 209.85.142.249 (209.85.142.249) 18.362 ms
9 216.239.40.66 (216.239.40.66) 30.822 ms 216.239.43.64 (216.239.43.64) 32.303 ms 216.239.40.69 (216.239.40.69) 32.281 ms
10 64.233.175.112 (64.233.175.112) 30.685 ms 72.14.237.139 (72.14.237.139) 28.956 ms 209.85.243.19 (209.85.243.19) 28.825 ms
11 216.239.59.3 (216.239.59.3) 29.805 ms 209.85.241.211 (209.85.241.211) 30.585 ms 216.239.59.3 (216.239.59.3) 30.537 ms
12 108.170.232.99 (108.170.232.99) 28.796 ms 28.691 ms 108.170.232.97 (108.170.232.97) 29.793 ms
13 lhr25s10-in-f14.1e100.net (216.58.198.174) 29.899 ms 30.860 ms 30.797 ms
Visually, we can see it this way:
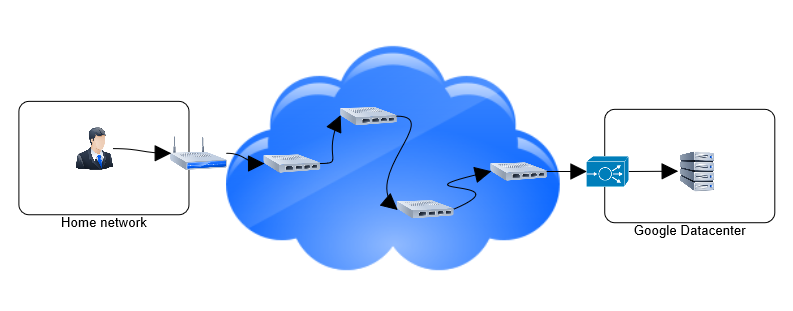
Each hop that I have to go through can be a potential security risk. Let’s take a look at two simple examples:
Eavesdropping
A malicious (or curious) person who can listen to traffic on your network can eavesdrop on your exchange with google.com:
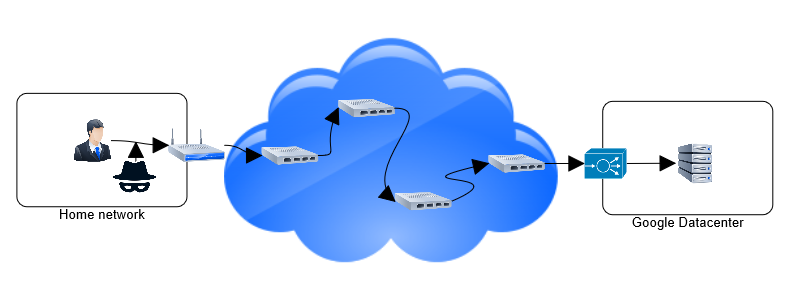
If the traffic on the network is pure HTTP, an eavesdropper can:
- Steals my account credentials through login forms.
- Captures my cookie or token ID to impersonate me.
- Stores sensitive information communicated over the network.
Man in the middle
A more sophisticated attacker can intercept your traffic and modifies the content before passing to the next hop. Anyone who control your network gateway or switch can be this “man in the middle”:
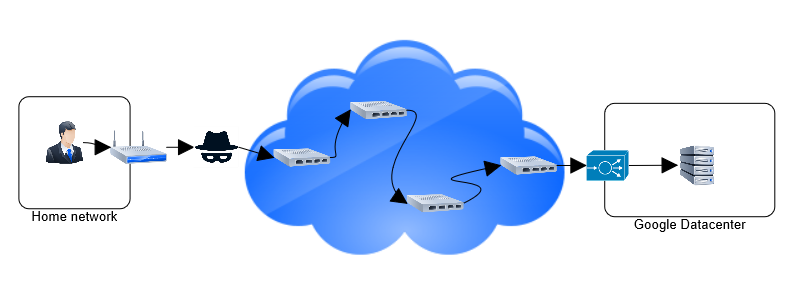
A man in the middle can do everything an eavesdropper can, and more:
- Sends me to a different server than the one requested.
- Modifies downloads to inject virus.
Can we secure the network somehow?
Unfortunately we don’t know how to migitate much of the network risks, at least not for the internet. But we can use encryptions to render these attacks ineffective by using HTTPS.
HTTPS advantages
A website served over HTTPS can guarantee two things to the client:
- Identity: it’s really the web site requested by the client and not a fake.
- Secrecy: the content exchanged between the client and the site can be understood only by the two parties and no one else.
How HTTPS works
How HTTPS works is rather elaborate; but for the purpose of our discussion we can simplify it as:
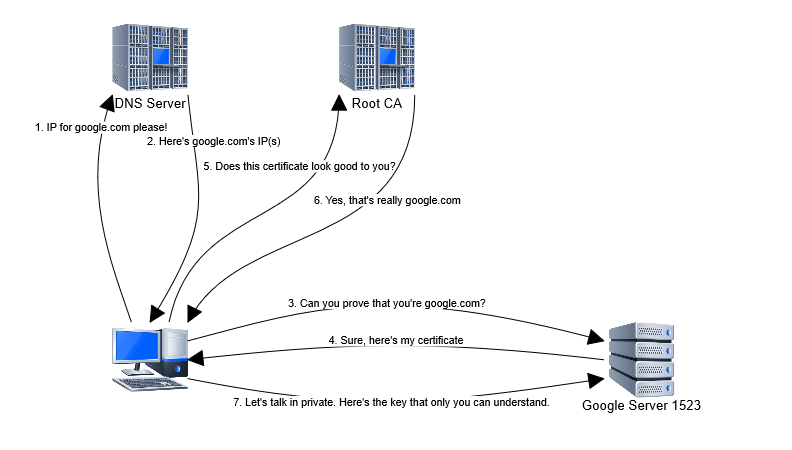
Three things that you should remember:
- The server must possess a public key that its annouces to connecting clients.
- The server uses its secret private key to authenticate itself to the client.
- The server key must be signed by a certificate authority to prove its validity.
To generate and sign the keys used to be somewhat costly and inconvenient. Fortunately, there is a recent player that seeks to disrupt the model: Letsencrypt.
Letsencrypt.org
A canadian non-profit organization; backed by some of the biggest players on the web.
Letsencrypt provides two things:
- The ACME protocol to simplify key generation and renewal.
- A public infrastructure to freely generate and renew keys.
Generate your first certificate
There are several ways you can generate certificates with Letsencrypt, here I’ll walk through the webroot method:
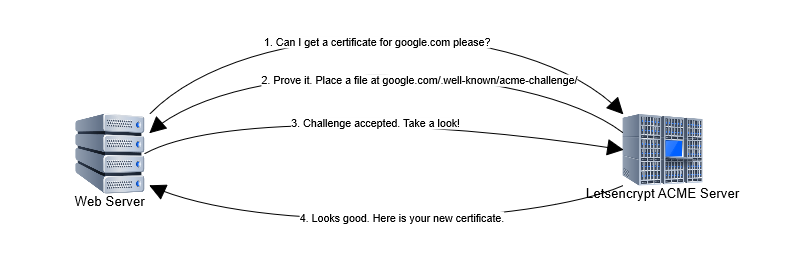
Basically, you need to prove to Letsencrypt that you control the domain by placing a file in the path: yourdomain.com/.well-known/acme-challenge/. After validation, Letsencrypt will sign your certificate and you can use that certificate to turn on HTTPS.
Doing this is rather straight-forward using the official Letsencrypt client and the nginx web server:
1. Install the client
su
cd /opt
git clone https://github.com/certbot/certbot
2. Prepare NGINX to serve the challenge
In your site’s configuration:
server {
listen 80;
…
location /.well-known/acme-challenge {
allow all;
root /tmp/letsencrypt;
}
}
Reload the configuration file with nginx -s reload
3. Generate the certificate
/opt/certbot/letsencrypt-auto certonly --webroot --webroot-path /tmp/letsencrypt -d mydomain.com --email=‘[email protected]’
The generated certificate is stored at /etc/letsencrypt/live/mydomain.com/
4. Turn on HTTPS
Modify the site’s configuration to enable HTTPS using the generated certificate:
server {
listen 80;
…
listen 443 ssl;
ssl_certificate /etc/letsencrypt/live/mydomain.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/mydomain.com/privkey.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH';
}
5. Automatic renewal
Renewal is as simple as running /opt/certbot/letsencrypt-auto renew
Put it in a crontab to run every day/week and you’re set.
Cloudfare
Another simple option to provide HTTPS to your site is through Cloudfare CDN. This blog is hosted by Github page but served by Cloudfare; therefore I get HTTPS for free.
Setting up Cloudfare is very easy. You do have to surrender DNS control to Cloudfare though so it’s certainly not everyone’s cup of tea. Head over to their website if you’re curious.